(SSH) How secure it is ?- TELNET & SSH
You may have tried using SSH connect a Virtual Machine (“VM”) in AWS/Azure/ GCP or others service provider , and their Data center is located somewhere in the world .
or
You want connect to a remote access network devices in the other city.
So that mean, the traffic will go through public internet network, then reach this VM. Peoples can capture the network traffic, if they want. All username, password will it exposed ? So what we do, Is it secure then?
Demonstration
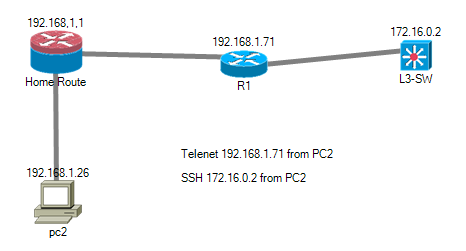
Now we will demonstrate it here. You can see image below: Figure 1.1
PC2 my computer is connected to a Home router.
& There is one router connected to my Home router.
Now I will use Wireshark capture the traffic on the PC’s interface, and we will find out what is the networking traffic will be like.
1. Connect to R1 by Telnet.
2. Connect to L3-SW by SSH
TELNET
First, you will configure your router such as Ip address, no shut, ip routing and allow using telnet .
Now I’m using window computer, telnet to 192.168.1.71, at the same time I’m using Wireshark to capture the traffic.
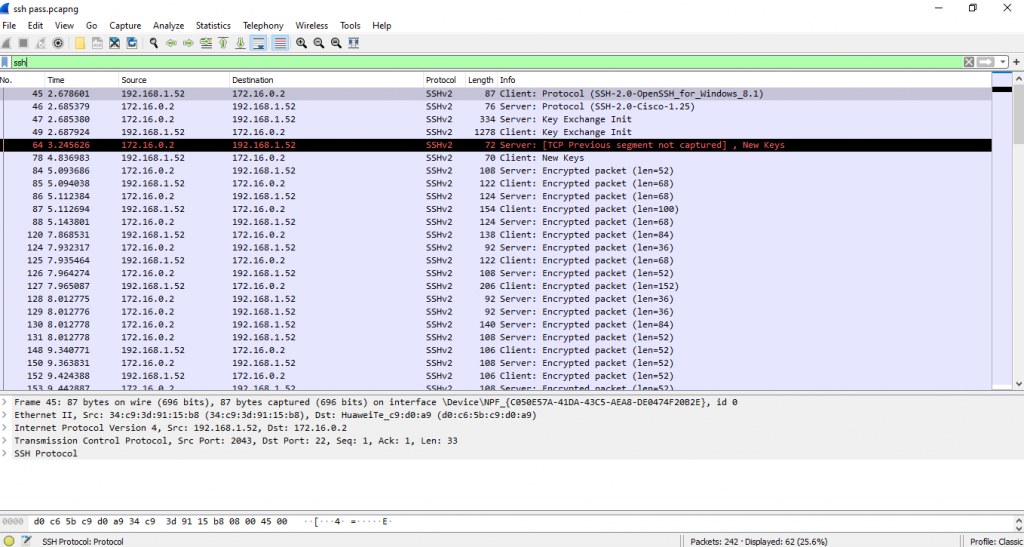
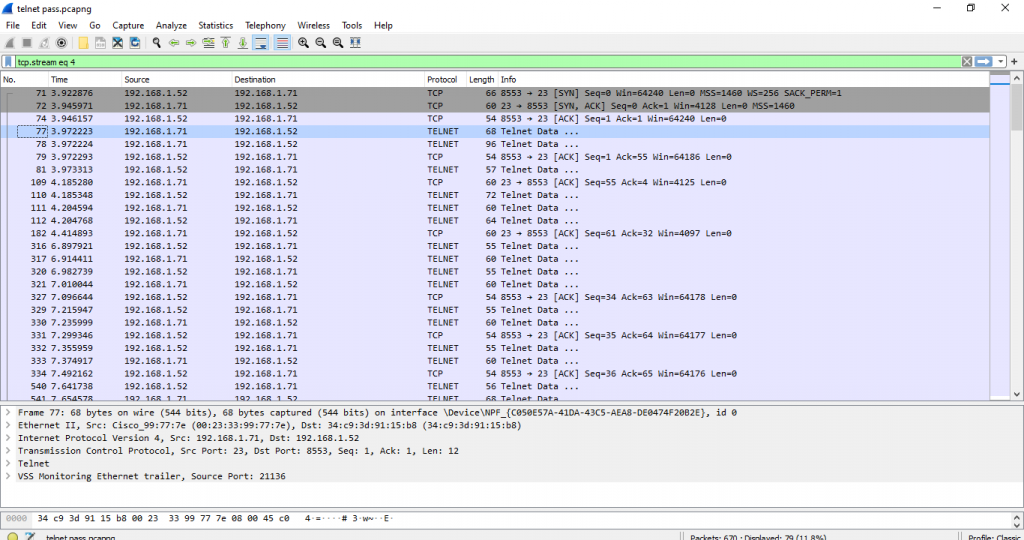
on figure 2.1, you want to filter the traffic, you only want to see Telnet. Information at the bottom, you will find Frame, Ethernet, intern protocol, Transmission control… It is refer to OSI MODEL 7 layer.
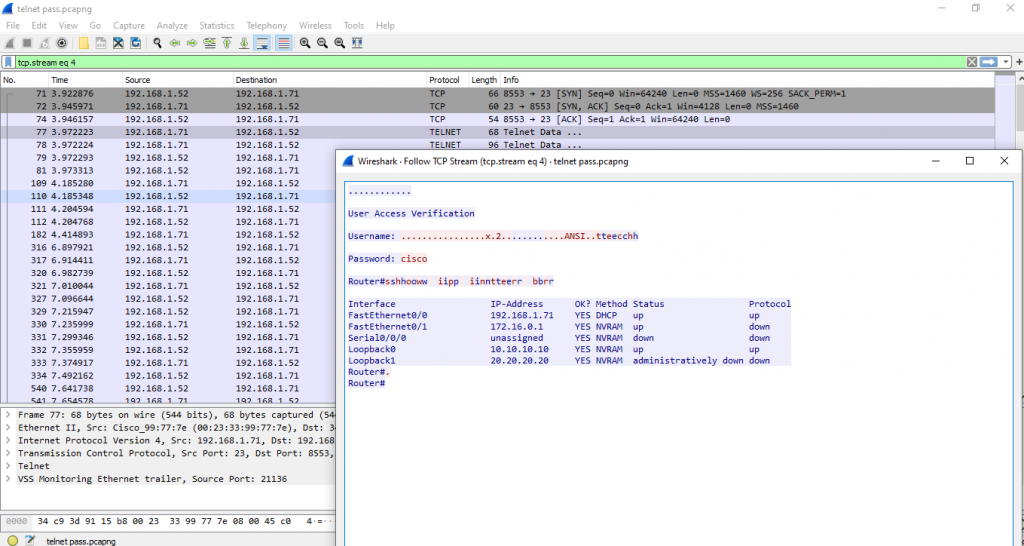
When we right click on one of the packet, “Follow the TCP stream“. You can see figure 2.2 image, it is a whole traffic that we do telnet.
BUT you can see username & password, also the commands result.
That’s Not Great.
SSH
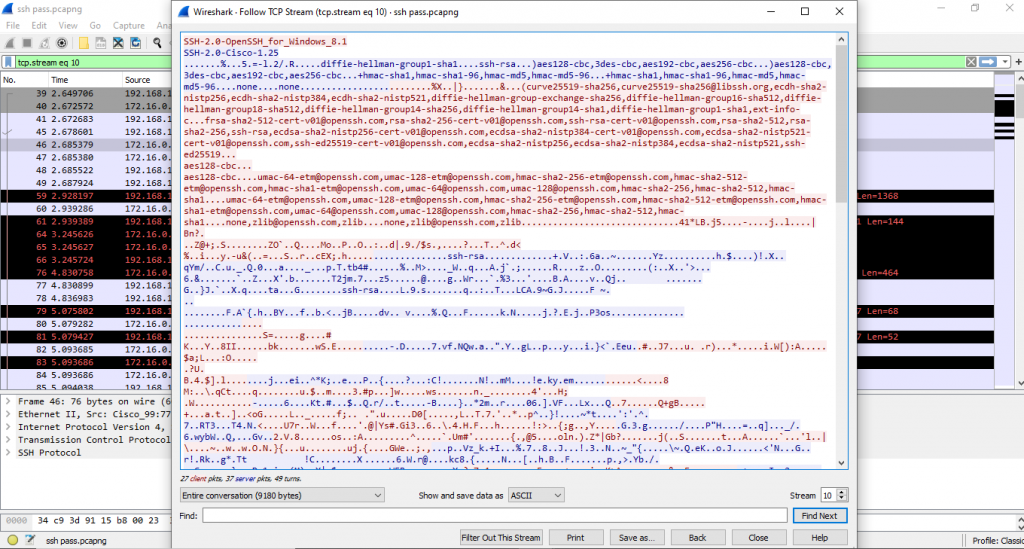
We do the same things here, But we use SSH to connect L3-SW switches. Also capture the traffic by Wire shark.
on figure 3.2, this time will still do the same. Follow TCP Stream. We know that something is happening here, we can’t understand.
Because it is encrypted. Secure Shell (SSH) will allow you operating network services securely over an unsecured network.