Diff AWS internet gateway – Cloudformation
INTRO
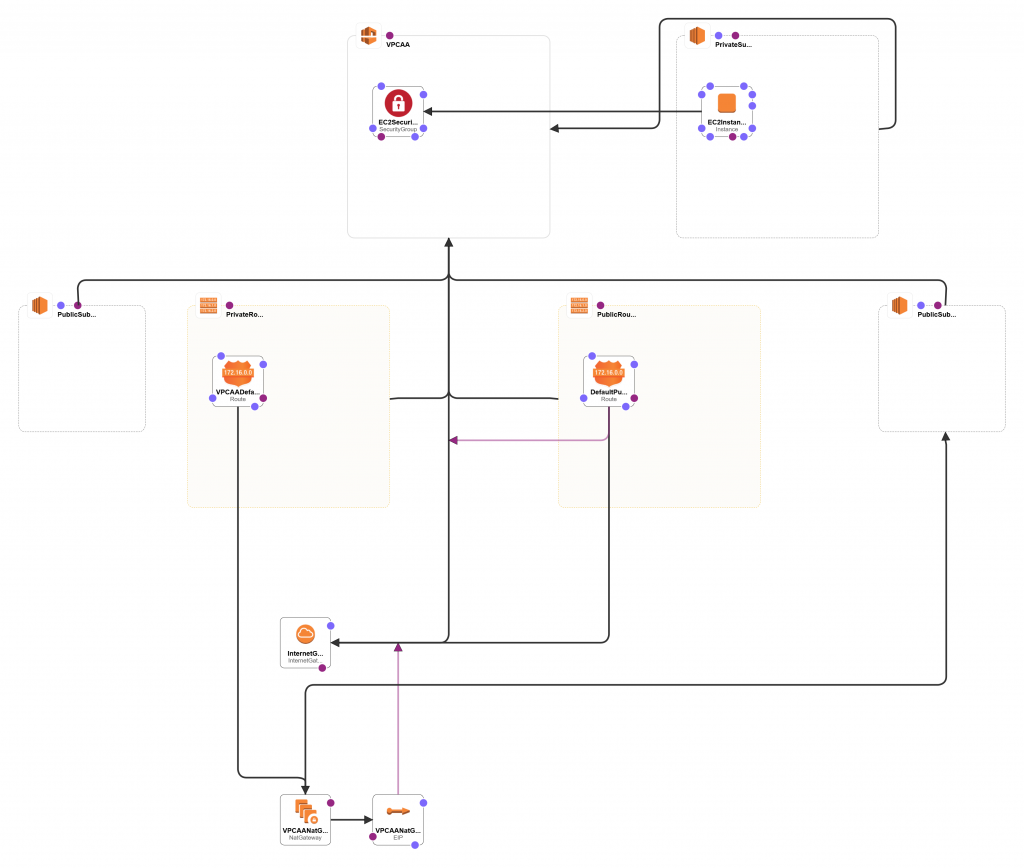
There different in AWS, for EC2 instances in private subnet to reach public internet. We will take a closer look at how AWS enables for different type in internet access. We will use cloudformation to build VPC, Subnets, internetgateway , NAT gateway and also with VM to test.
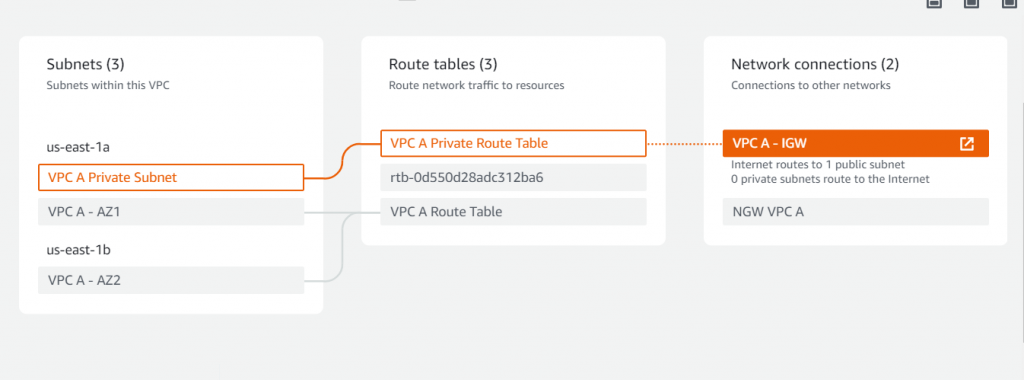
Internet Gateway – It serves as the entry and exit point for internet traffic to and from your VPC.
NAT Gateway – IPV4
Egress-only Internet gateway – IPV6
Diagrams
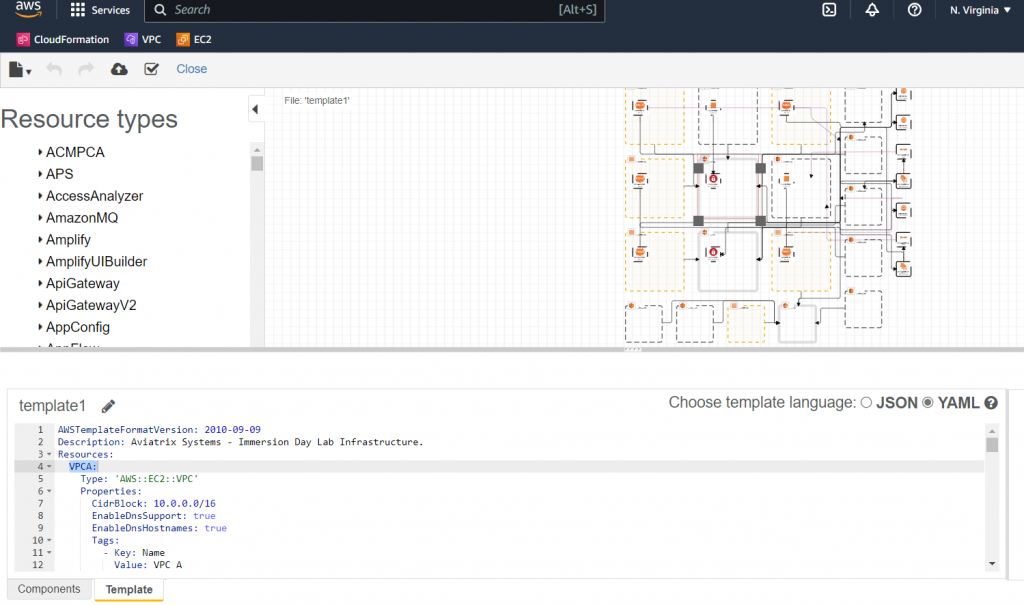
At the bottom of the page, you can find cloudformation code. Bascially, you can save it in a text file. In Cloudformation, upload the text. It will create & store it in your S3 Bucket. Next you can open up Desgin template to review or modify.
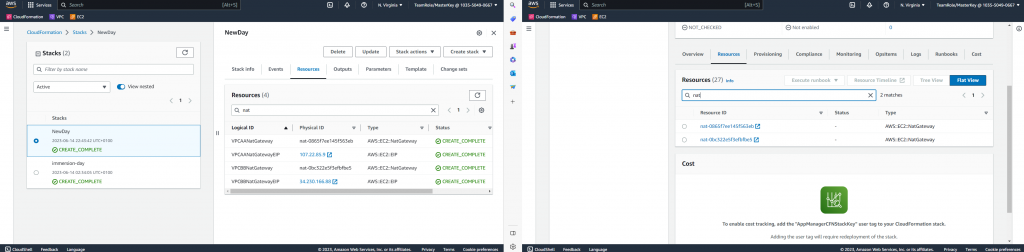
Comparing with Terraform and Cloudformation. They are both infrastructure as code. If you use Cloudformation, you can view your resources under cloudformation stack in AWS application manager. Also you can view the status of the related EC2 .
Internet Gateway – bind EIP to Instance
If we use internet gateway , bind EIP to EC2 instance. It will allow your instance to reach public internet. Also at the same, your instance inbound port is opened as well. It will reply on your security group to allow specific port to open. Also EIP is binding to 1 instance.
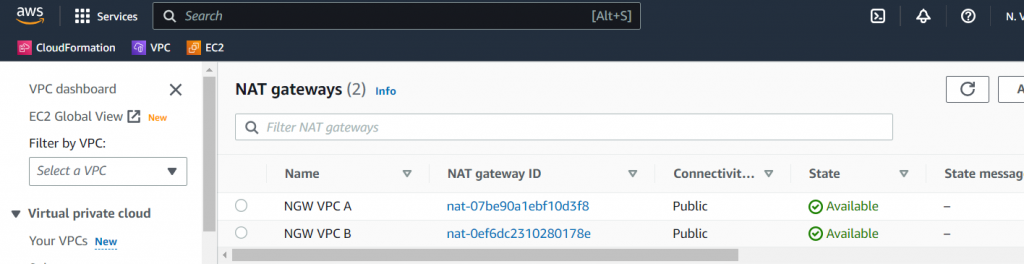
NAT Gateways for Secure Internet Access:
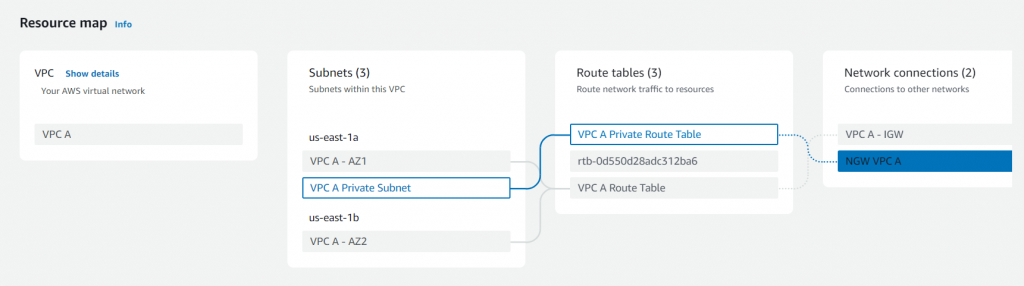
NAT Gateways act as a bridge between the private subnets and the internet, allowing resources within the private subnets to access external services while preventing inbound connections from the internet. In our infrastructure example, each VPC has a dedicated NAT Gateway associated with its respective public subnet.
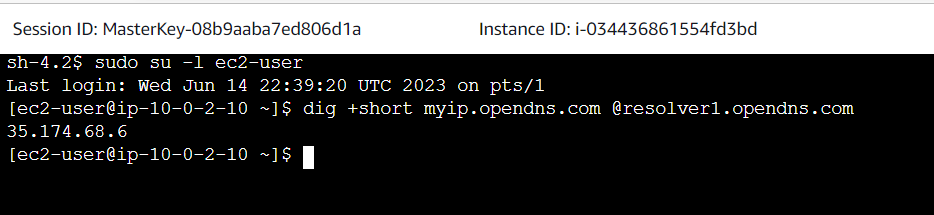
Result
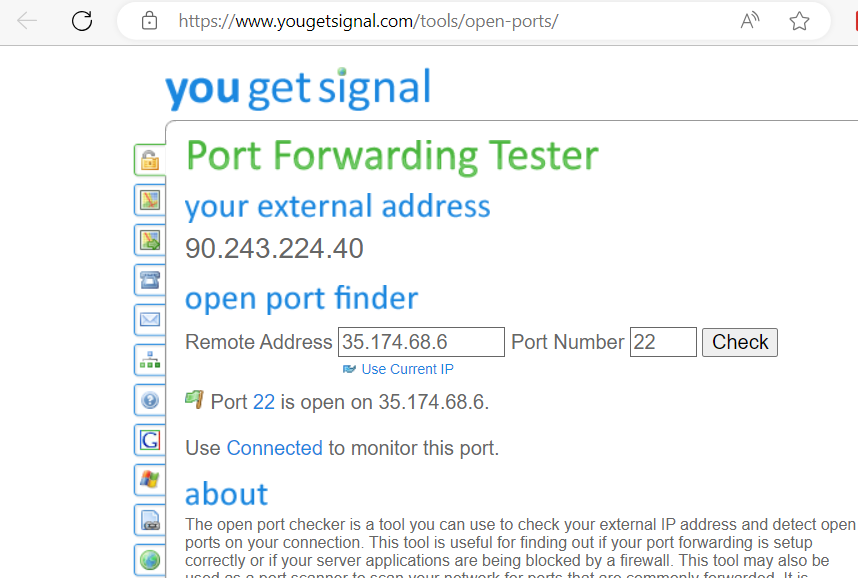
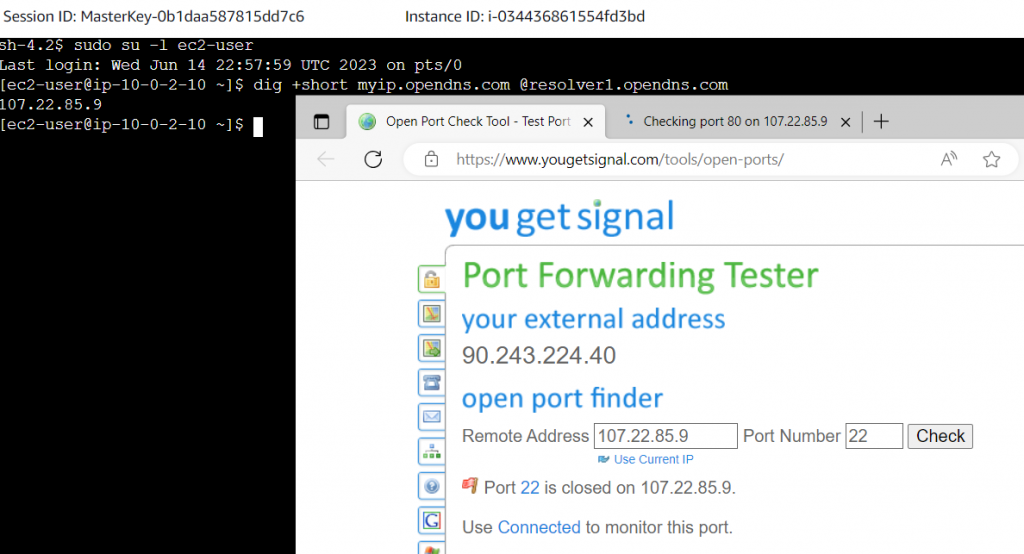
Internet Gateway EIP – Obtained an public ip 35.174.68.6. when we use port scanner to scan, port 22 is open in the public.
NAT Gateway – Obtained an public ip 107.22.85.9 Same EC2 instance and same Security group, but we are using NAT gateway. Port 22 is closed this time by using port scanner.
By using this AWS CloudFormation template, wecan create a secure cloud infrastructure that separates their resources into VPCs, establishes public and private subnets, and enables outbound internet connectivity for private resources via NAT Gateways. The template automates the deployment process, making it easier to create consistent and secure cloud architectures.
CloudFormation Code
AWSTemplateFormatVersion: '2010-09-09'
Description: Aviatrix Systems - Immersion Day Lab Infrastructure.
Resources:
# Create VPCs with public subnets
VPCAA:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 10.0.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
Tags:
- Key: Name
Value: VPC A
InternetGatewayA:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: VPC A - IGW
InternetGatewayAttachmentA:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
InternetGatewayId: !Ref InternetGatewayA
VpcId: !Ref VPCAA
PublicSubnetA1:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPCAA
AvailabilityZone: !Select [ 0, !GetAZs '' ]
CidrBlock: 10.0.0.0/24
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: VPC A - AZ1
PublicSubnetA2:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPCAA
AvailabilityZone: !Select [ 1, !GetAZs '' ]
CidrBlock: 10.0.1.0/24
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: VPC A - AZ2
PublicRouteTableA:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPCAA
Tags:
- Key: Name
Value: VPC A Route Table
DefaultPublicRouteA:
Type: AWS::EC2::Route
DependsOn: InternetGatewayAttachmentA
Properties:
RouteTableId: !Ref PublicRouteTableA
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGatewayA
PublicSubnetA1RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PublicRouteTableA
SubnetId: !Ref PublicSubnetA1
PublicSubnetA2RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PublicRouteTableA
SubnetId: !Ref PublicSubnetA2
# Create private subnets
PrivateSubnetA:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPCAA
AvailabilityZone: !Select [ 0, !GetAZs '' ]
CidrBlock: 10.0.2.0/24
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: VPC A Private Subnet
PrivateRouteTableA:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPCAA
Tags:
- Key: Name
Value: VPC A Private Route Table
PrivateSubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PrivateRouteTableA
SubnetId: !Ref PrivateSubnetA
# Create EC2 Instances
EC2InstanceA:
Type: AWS::EC2::Instance
Properties:
ImageId: ami-087c17d1fe0178315 #AL2 us-east-1
BlockDeviceMappings:
- DeviceName: /dev/sda1
Ebs:
VolumeSize: '8'
VolumeType: gp2
Encrypted: 'true'
DisableApiTermination: 'false'
KeyName: ee-default-keypair
InstanceType: t3.micro
IamInstanceProfile: Ec2RoleForSSM
NetworkInterfaces:
- DeviceIndex: '0'
PrivateIpAddress: '10.0.2.10'
GroupSet:
- !Ref 'EC2SecurityGroupA'
SubnetId: !Ref 'PrivateSubnetA'
Tags:
- Key: Name
Value: EC2 A
- Key: Environment
Value: Development
EC2SecurityGroupA:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: 'EC2 VPC A - AZ1'
VpcId: !Ref 'VPCAA'
SecurityGroupIngress:
- IpProtocol: icmp
CidrIp: '10.0.0.0/8'
FromPort: 8
ToPort: -1
Tags:
- Key: Name
Value: EC2 A Security Group
VPCAANatGatewayEIP:
Type: AWS::EC2::EIP
DependsOn: InternetGatewayAttachmentA
Properties:
Domain: vpc
VPCAANatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt VPCAANatGatewayEIP.AllocationId
SubnetId: !Ref PublicSubnetA1
Tags:
- Key: Name
Value: NGW VPC A
VPCAADefaultPrivateRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateRouteTableA
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref VPCAANatGateway