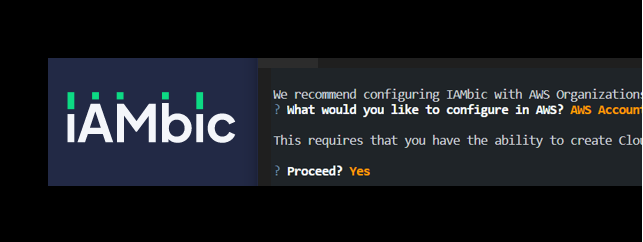
IAMBIC to manage AWS IAM
When there is so many policy, rules, users you need to manage on AWS account. IAMBIC may help you to manage these. Better way to manage permission on different user such as contractor, developer….etc , also it can be accross organization in different accounts.
INSTALLATION
https://docs.iambic.org/getting_started/configuring_iambic
Iambic can be run on windows, linux and MAC. Before you install it, please makesure you have python, git & AWS CLI installed.
Then let’s run
python3 -m venv venv
source /venv/Script/activate
pip install iambic-core
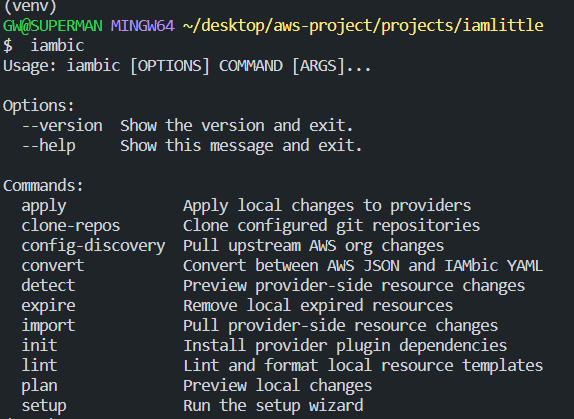
SETUP
iambic setupGoing through the iambic setup, You will be asked for AWS account, IAM user, access key & secret key.
and other type of questions, do you allow iambic to create role…etc
Remember to select ‘Yes’ for importing current config from your aws account.
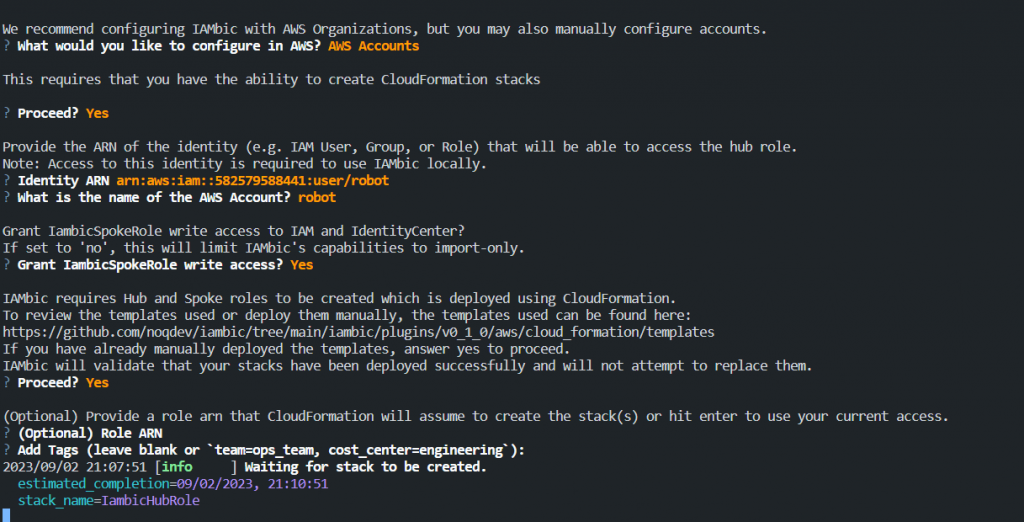
After setup process is completed.
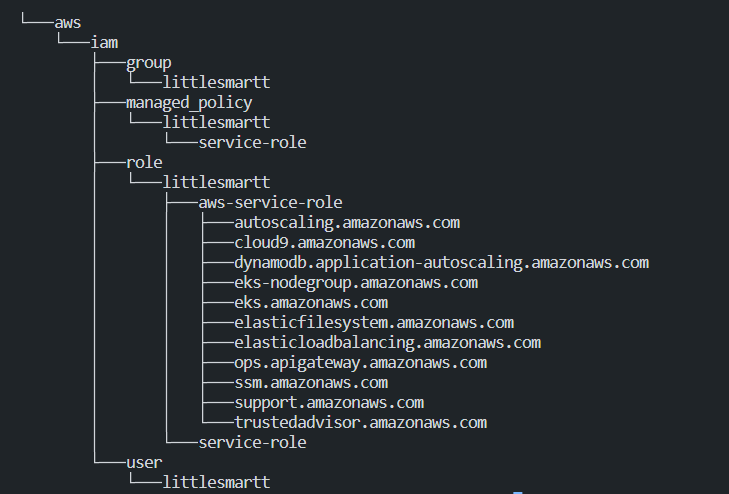
You will notice there will be a lot YAML, folder has been created under your Folder.
- Group -> it is group that you assigned to users.
- managed_policy -> Policy that you attached to group/ users.
- role -> roles that apply to other AWS services such ec2, lambda…etc
- user -> user
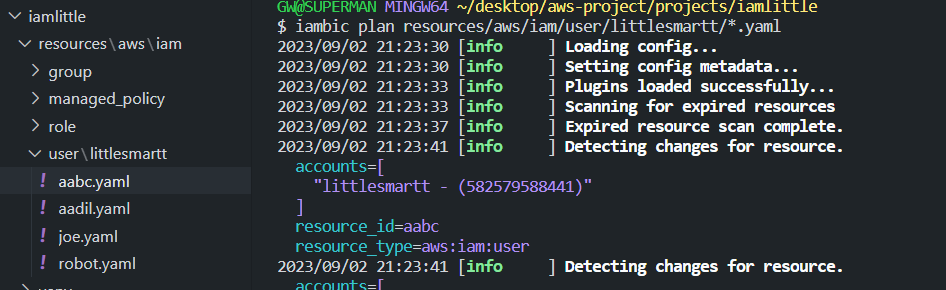
How to use
Iambic will import user, policy, role, group to your local repository.
- Add a new group – “iambic”
- Add a new user with the group “iambic”
- Create a new user.yaml file under user folder & also group.yaml under group.
#For user yaml file
template_type: NOQ::AWS::IAM::User
template_schema_url: https://docs.iambic.org/reference/schemas/aws_iam_user_template
included_accounts:
- littlesmartt
identifier: aabc
properties:
groups:
- group_name: Code
- group_name: IMTEST
- group_name: Web_Server
managed_policies:
- policy_arn: arn:aws:iam::aws:policy/AmazonEC2FullAccess
user_name: aabc
#For group yaml file
template_type: NOQ::AWS::IAM::Group
template_schema_url: https://docs.iambic.org/reference/schemas/aws_iam_group_template
included_accounts:
- littlesmartt
identifier: IMTEST
properties:
group_name: IMTEST
managed_policies:
- policy_arn: arn:aws:iam::aws:policy/AWSHealthFullAccess
iambic plan resouces/aws/iam/group/*.yaml resources/aws/iam/user/*yaml
iambic apply resouces/aws/iam/group/*.yaml resources/aws/iam/user/*yaml
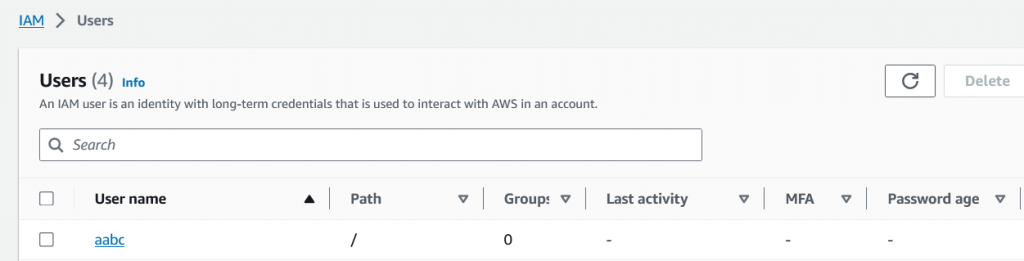
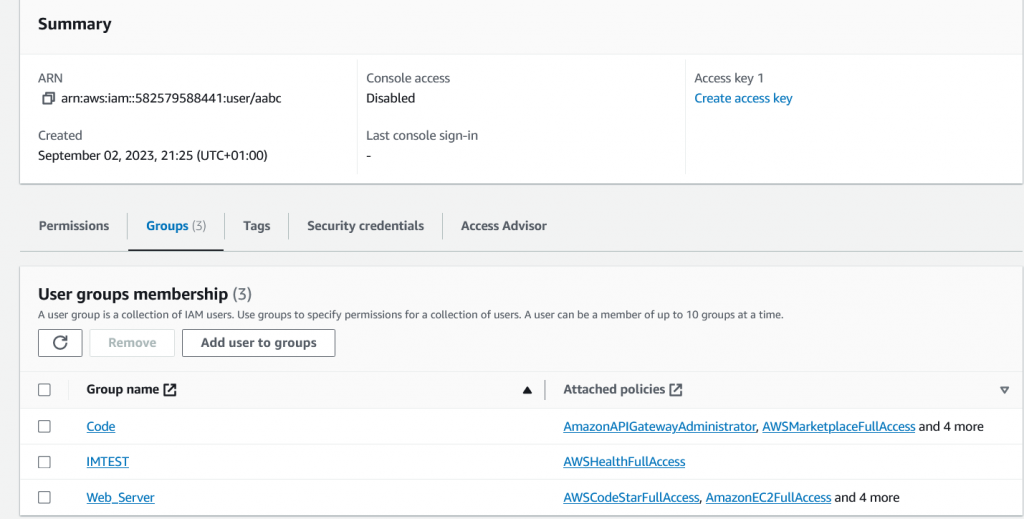
Back to AWS Portal, on IAM sectin. we can see user and Group has been created.
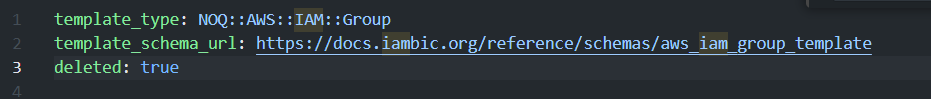
If you want to delete the user/ group , which you just created.
added -> “deleted: true” in the yaml file.
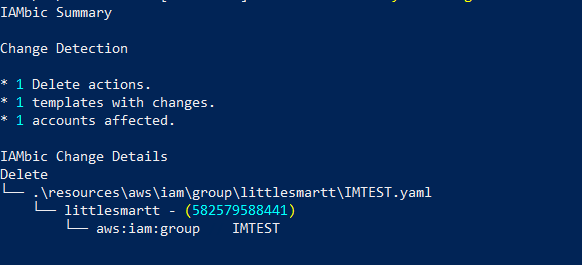
After you run the iambic apply …/
The file will be deleted after.
Thanks for reading
🙂