Reach to internet via other firewall in AWS
Internet
In previous post, in order to secure our VM in the private subnet. Using NAT Gateway, is very good option. In the other hand, AWS will charge it on the NAT Gateway usage. below info:
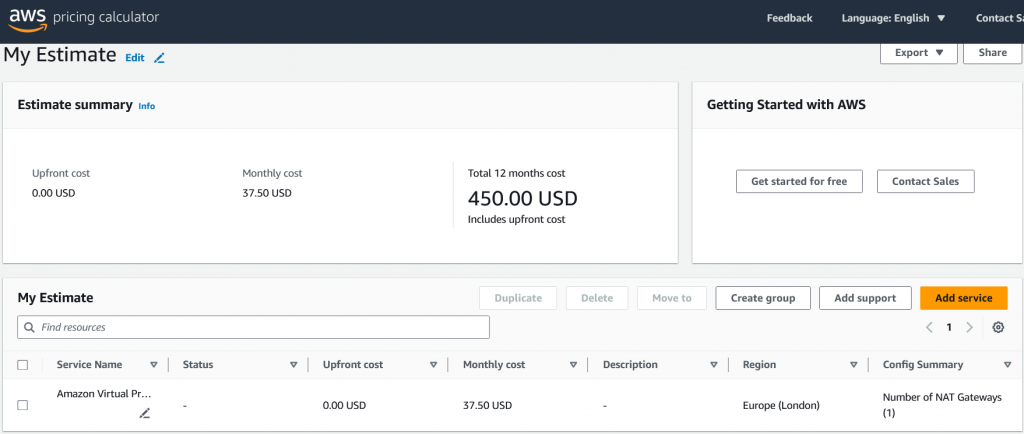
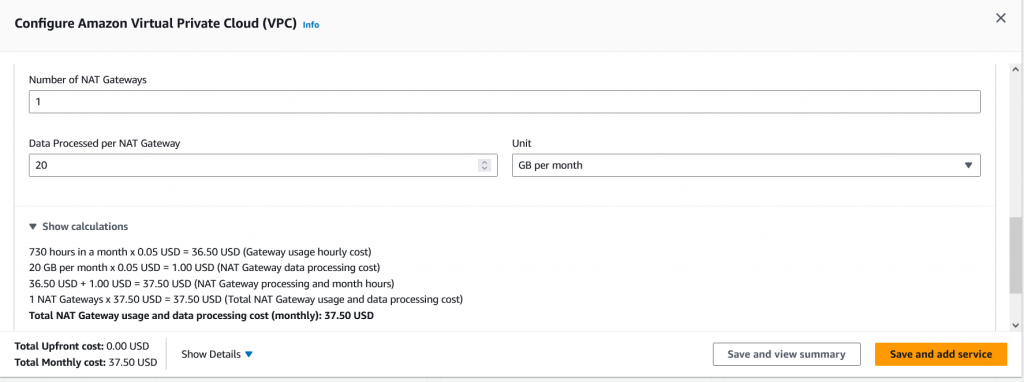
NAT gateway will do NAT gateway do. It will not filter specific URL…..or other function. In this case, we can put third party firewall act as Gateway and also we can apply firewall policy to restrict the traffic.
Deploy Fortigate Firewall
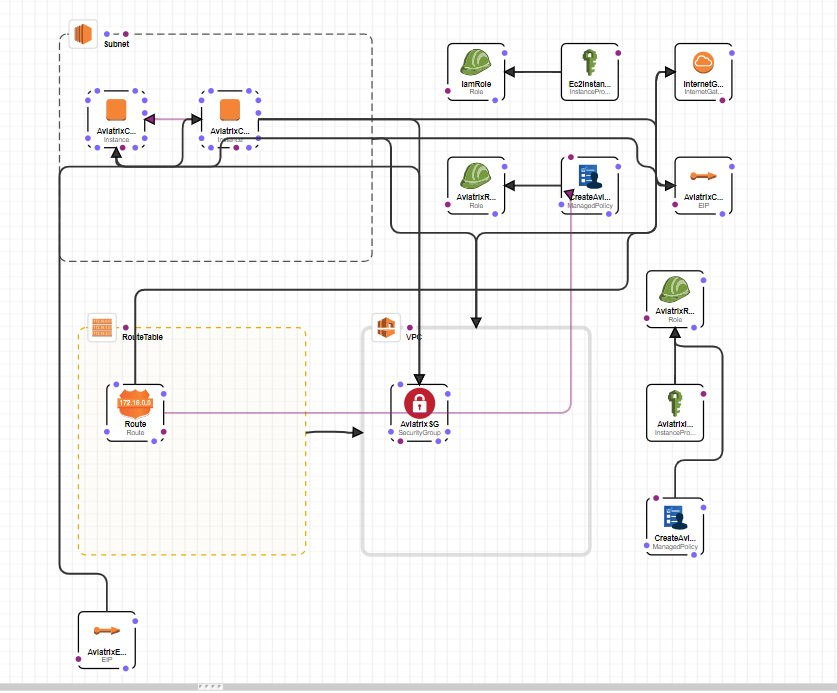
1 VPC
1 Public Subnet + 1 Private Subnet ( Also Routing table )
1 Internet Gateway
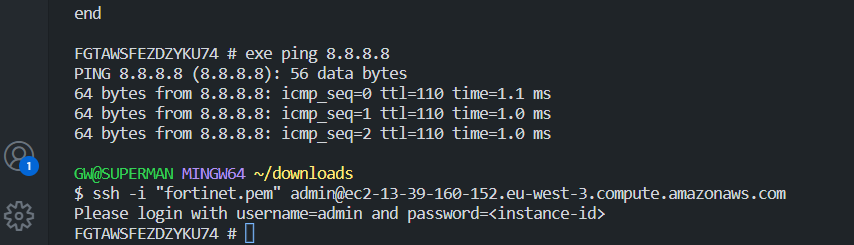
1 VM in Public subnet & 1 VM ( Ubuntu ) in Private SubnetUnder AWS Marketplace you could select fortigate to deploy, beware pricing on the conditions. First, when you launched the Fortigate in AWS. You can login to Fortigate via HTTPS.
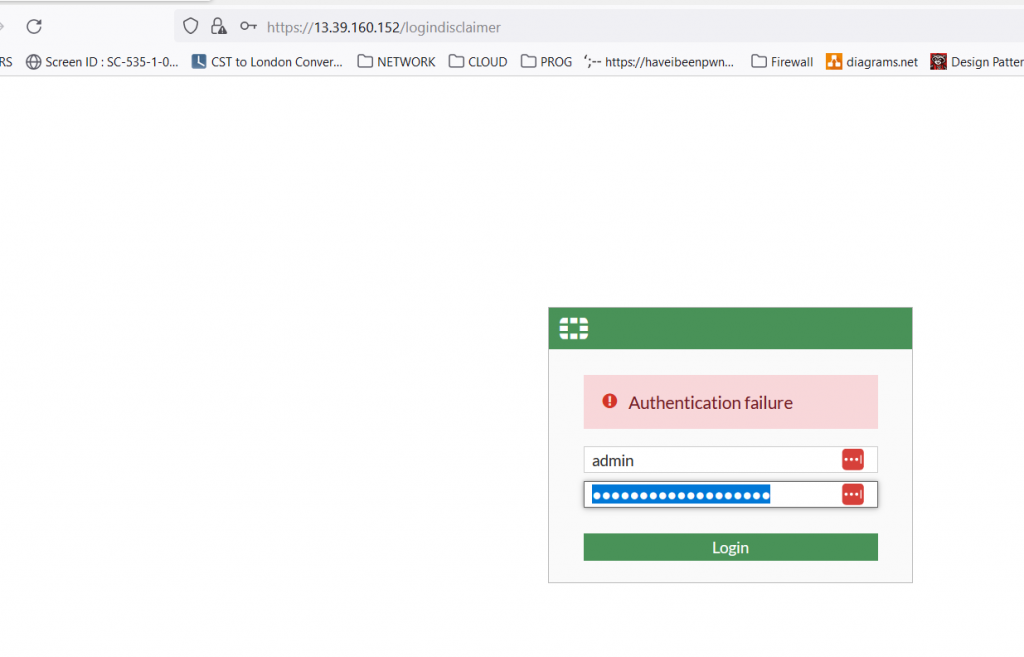
NAME: admin
Pass: will be your instance ID ( <- go to AWS EC2, you can find your instance ID info ) 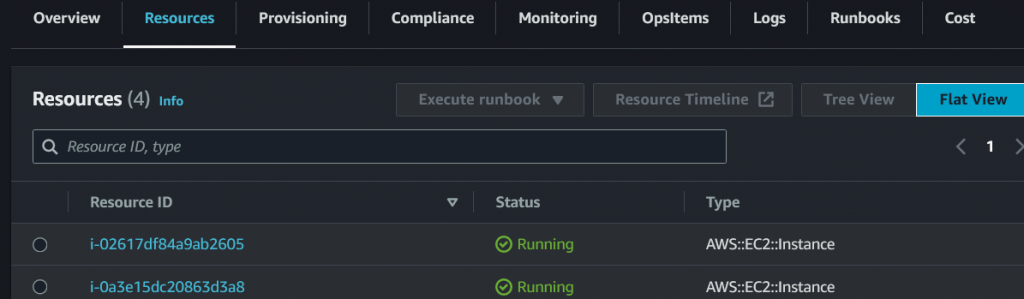
apply rules with related IP:
- Virtual IP -> for ssh into your VM in private subnet
- Firewall rules for ssh flow
- Explicit Proxy on Fortigate
- Proxy firewall ruels 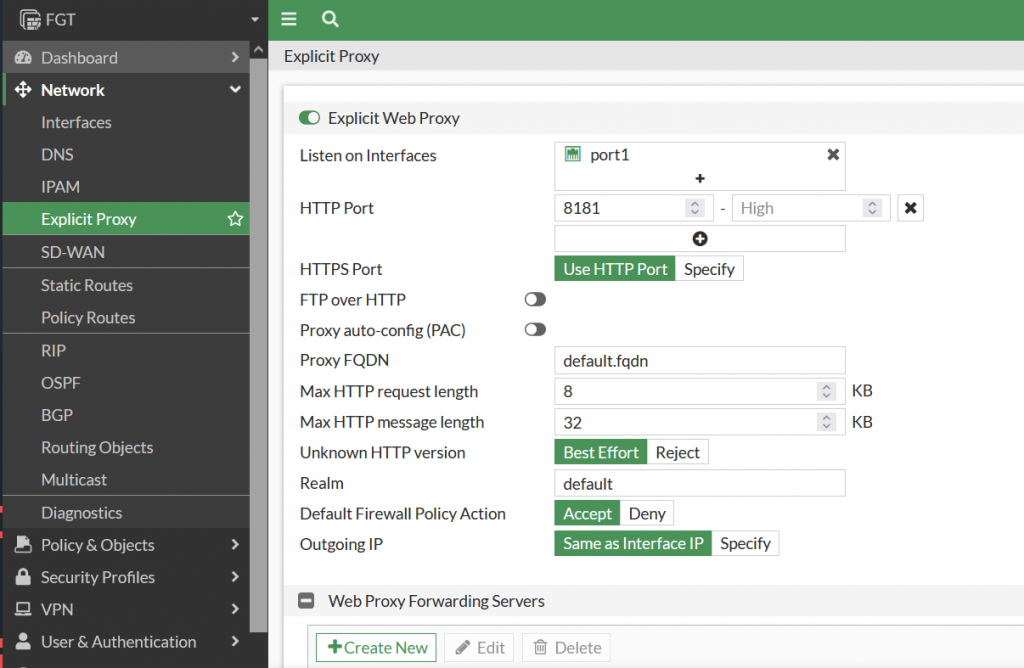
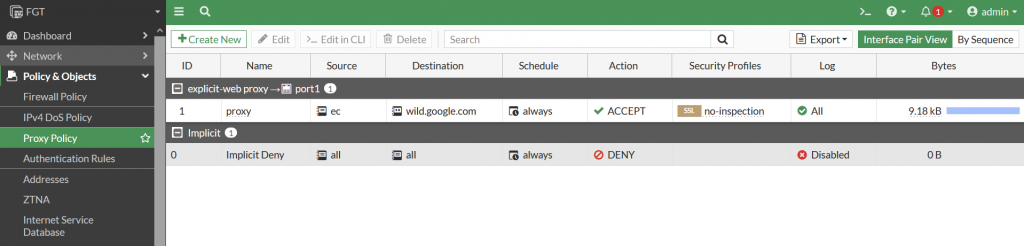
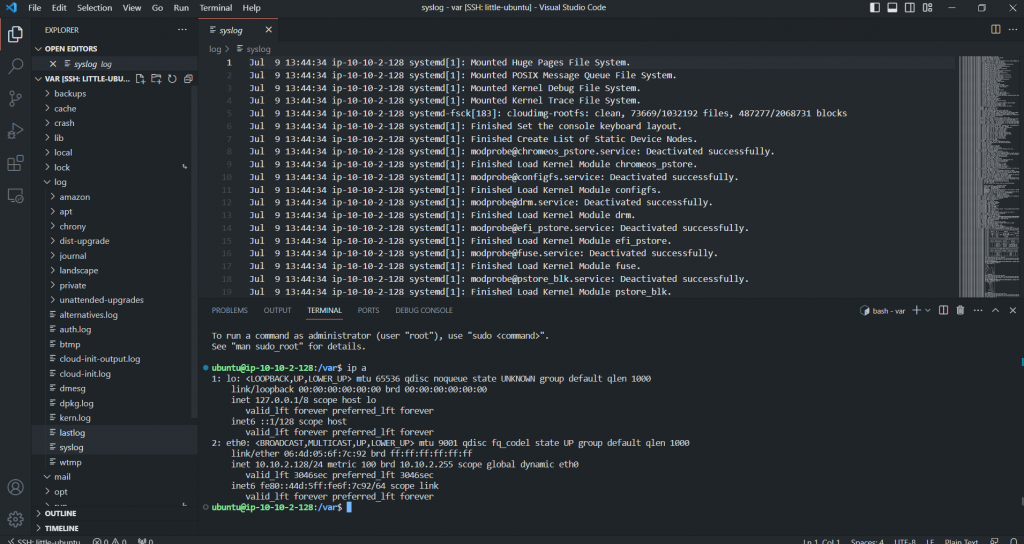
Fortigate has been setup, now we moved the VM in Private Subnet.
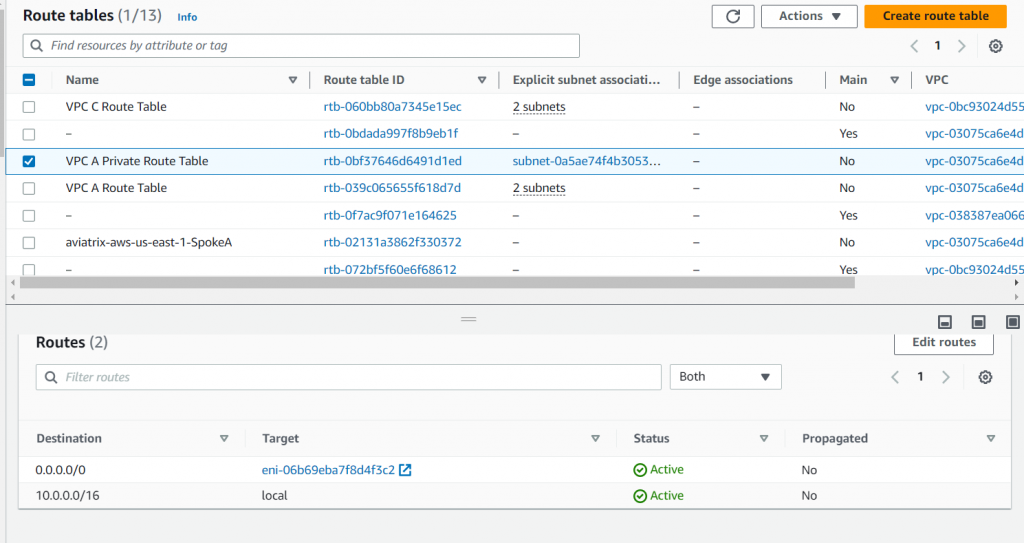
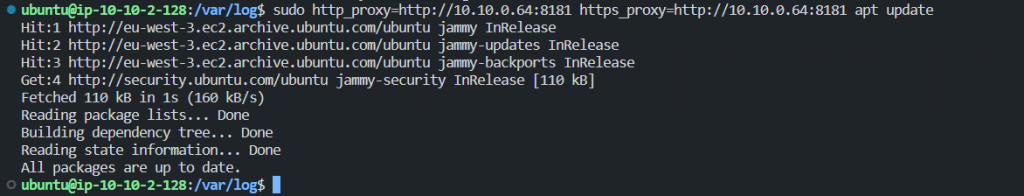
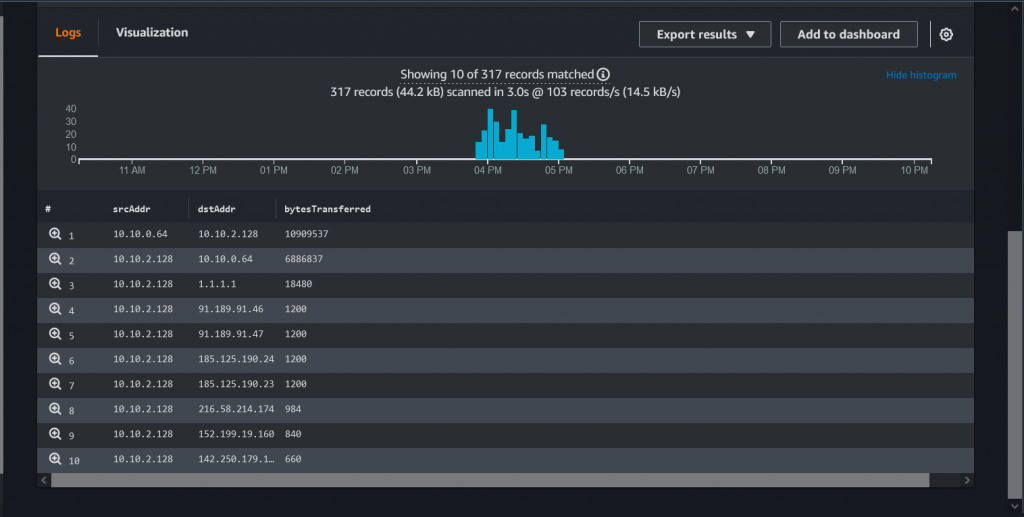
This is Ubuntu VM with prviate Ip 10.10.2.128. Can reach to the internet via Fortigate Proxy ( Google website, apt update, apt install….etc) Also on Fortigate, we can restrict HTTPS & HTTPS on services, and FQDN for the DST .
Aviatrix Firewall
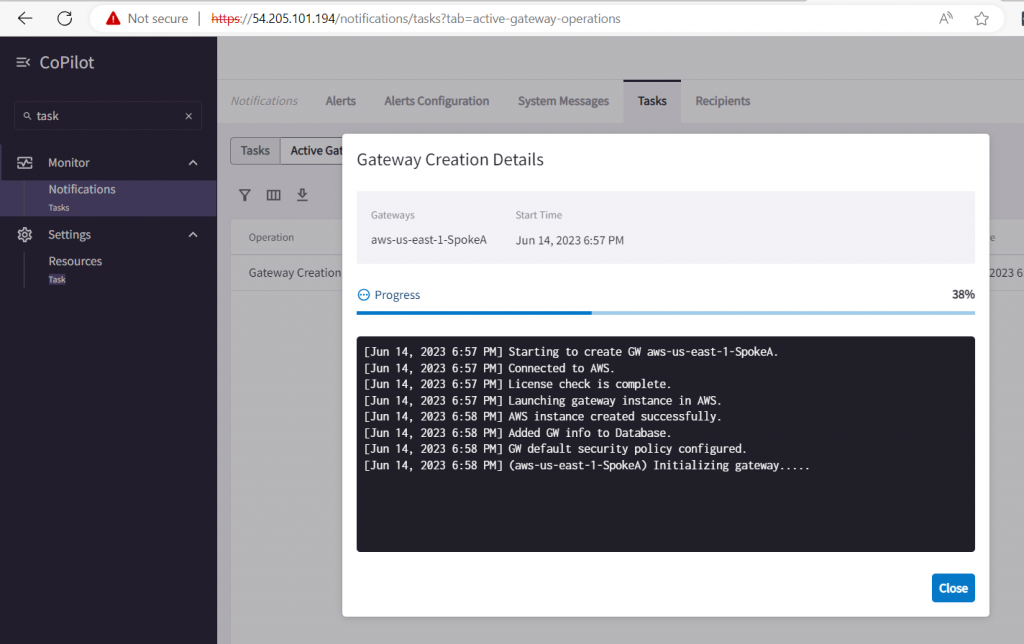
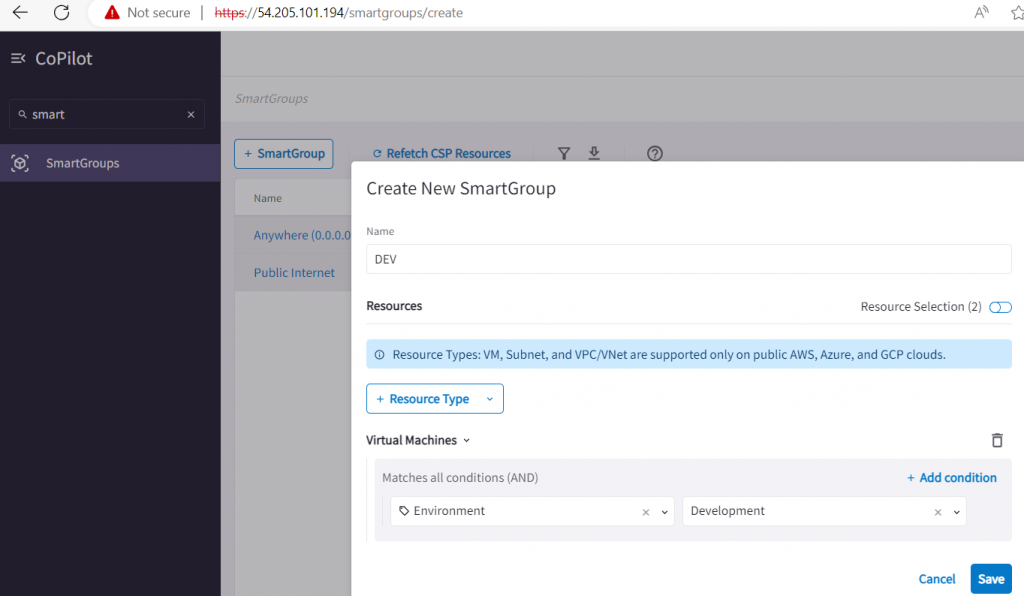
If you are using Aviatrix in your work enviroment. You can also use it’s Distributed firewall to inspect the traffic. After the distributed Firewall is active. Then search “smartgroup” at the left hand side . You will configure your smartgroup.
will need to define which is enviroment -> development, production…etc
Can Development traffic go to production
Can Development traffic go to Public internet