Sentinel helping you in Terraform
How to make sure standard format or practising , enforce accross to all terraform user. In Terraform Cloud / Terraform enterprise is allowing your to put sentinel policy in place.
Prevent certain actions or configurations that may violate your organization’s compliance or security standards
Being with Terraform Cloud
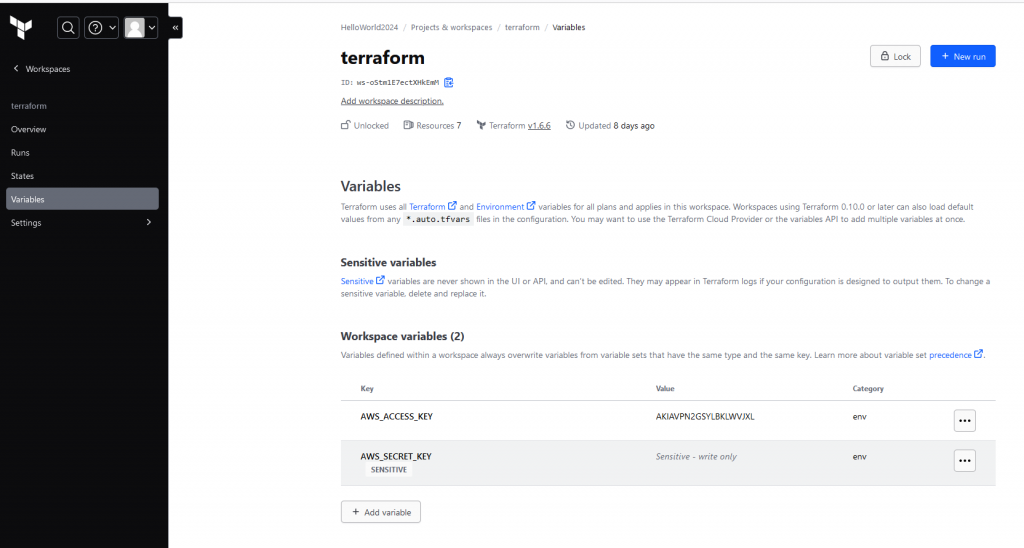
Using terraform with Github responsitories. You can trigger the run on each push by Github. Also for sure, you will not like to put your AWS credential in github. you can use Enviroment variable in terraform Cloud.
Once we have written terraform main code. This time we push the code with no Tags within our AWS resources.
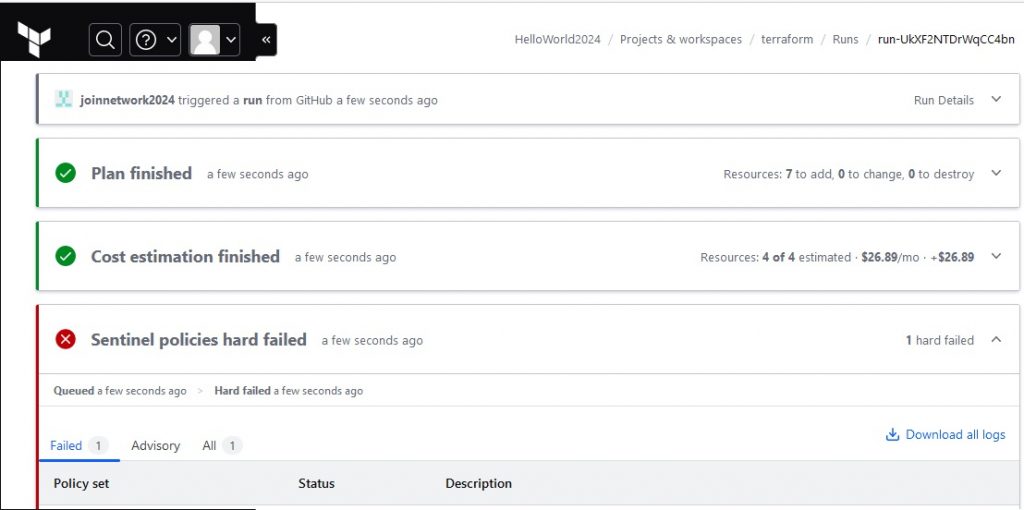
With our Sentinel intergrated policy that we use, after Terraform Cloud run the tf files.
- we can see resouces plan, that will deploy
- we can see how much monthly cost for those resouces
- Also we can see Red, Deny by Sentinel policy.
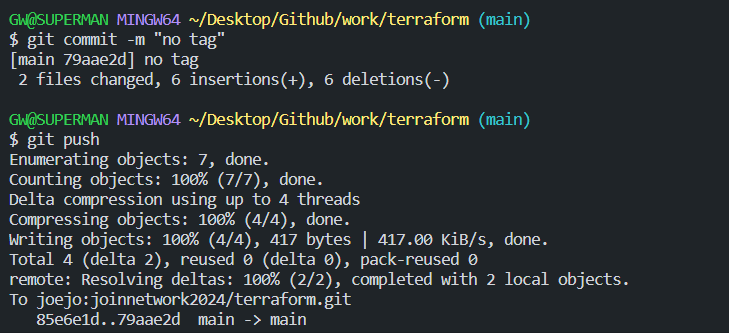
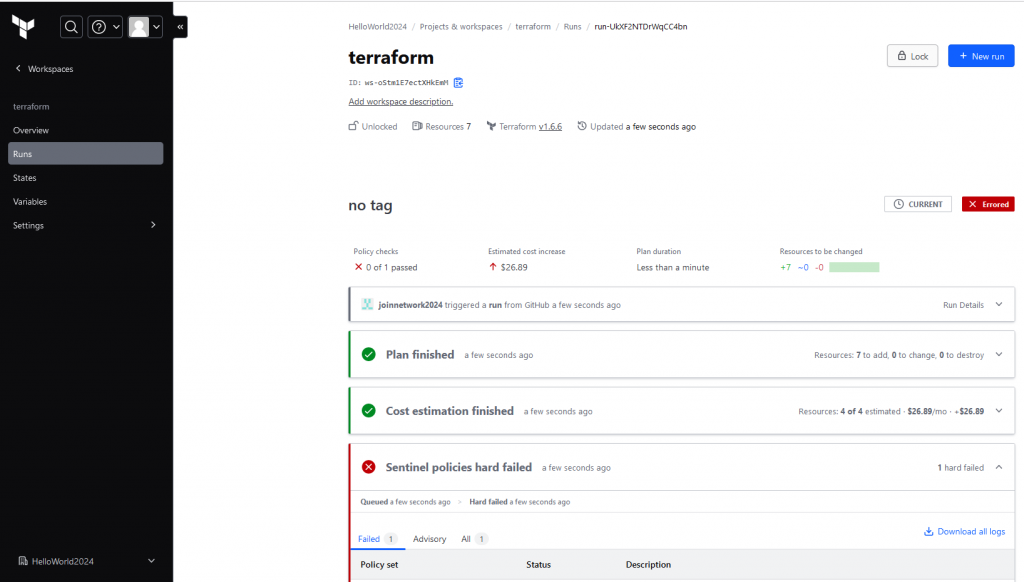
Let’s do another push , with Tags for AWS instance resources.
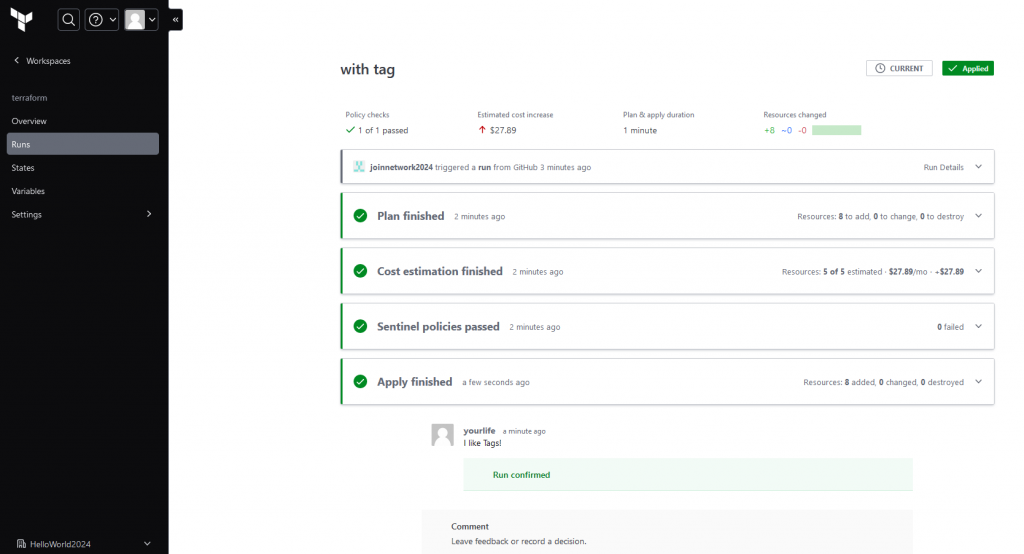
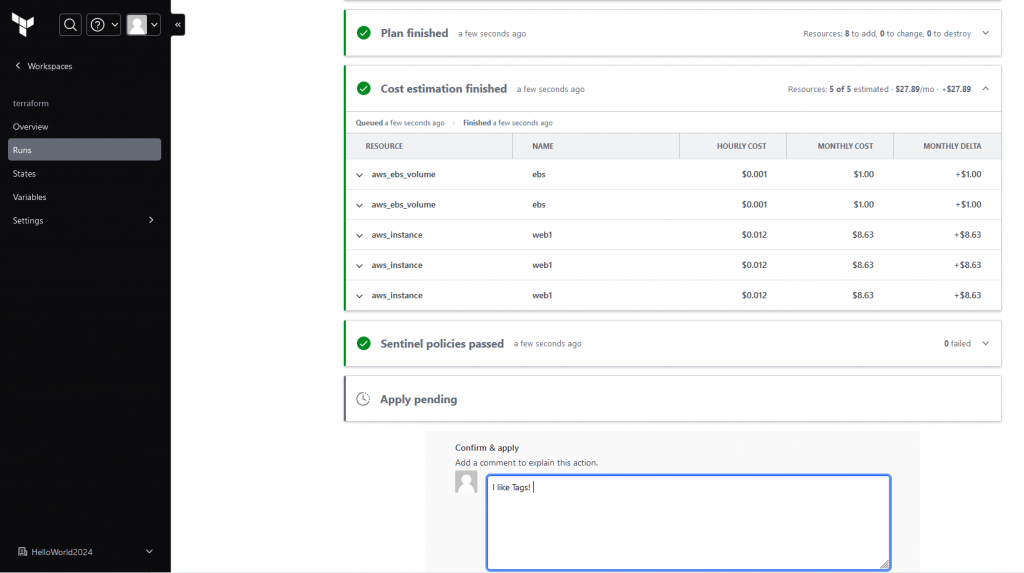
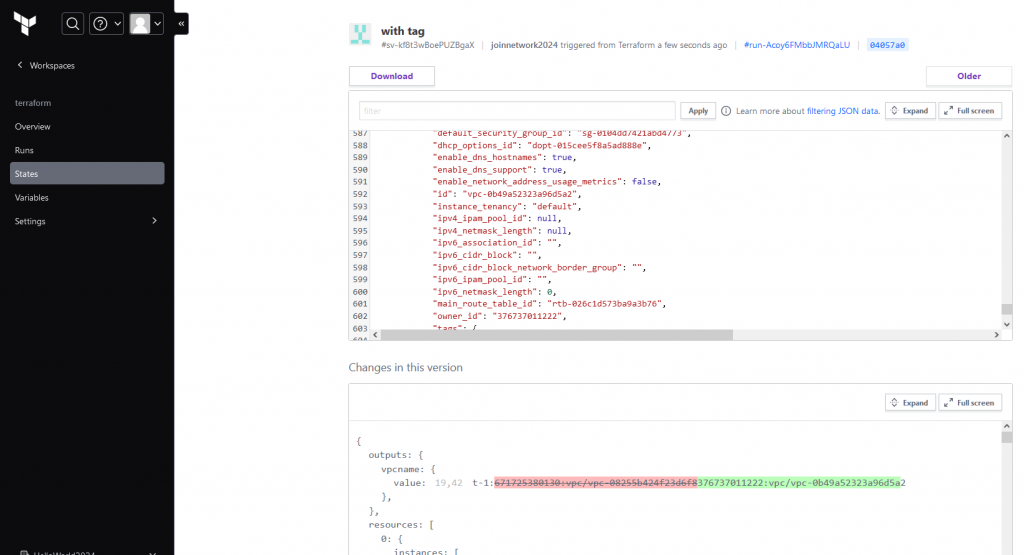
With the Tags, we can now successfully deploy resouces to AWS via terraform cloud. Under the states files, we can see the state files as usual, what we see in free version Terraform. This time, it is stored in remote backend by managed by HashiCorp.
We may able to see the diff, compare with previous state.
Sentinel Policy
Now we will look into the policy set which will apply to all run in the workspaces. How it stop users to apply terraform.
- tfplan is terraform plan files – need to import this modules
- main = rule -> rule basically is this how to run
- within the rules. in each AWS instance, if the tags length is greater than 0. Which mean it is “True”
- When it is True, will pass the policy.
Thanks for readings ^^